WordPress Disable XML-RPC Prevent XML-RPC DDoS
If you do not need this feature in WordPress disable XML-RPC. The xmlrpc.php file in WordPress allows users to perform remote actions with their website.XML-RPC DDoS and another XML-RPC attack such as brute force take advantage of this feature.
WordPress Disable XML-RPC Instructions
Install A WordPress Security Plugin
The easiest was to disable the XML-RPC feature for WordPresss is to use a plugin:
- Step 1: Install and activate Security Safe.
- Step 2: Find the Security Safe menu item on the left panel in the WordPress admin and click on it.
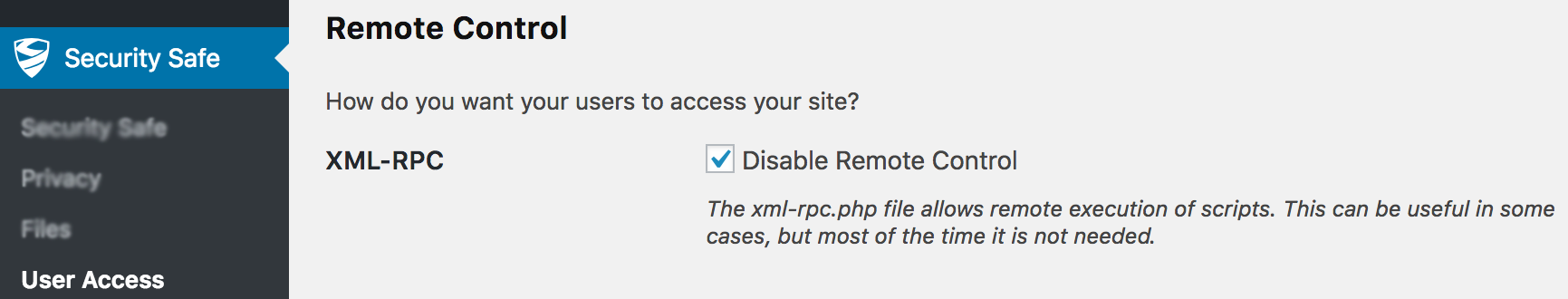
- Step 3: Click on the “User Access” menu item at the top of the page. This will take you to a settings page where you can enable/disable features of the plugin.
- Step 4: Scroll down the page until you see the XML-RPC setting. Click the checkbox to disable XML-RPC then scroll down and click “Save Settings.”
Add Custom Code To Your Theme
If you are comfortable modifying php code, then do the following:
- Step 1: edit the functions.php file of your theme or child theme. NOTE: If you have purchased a theme that receives updates, you may want to ensure that you are editing the child theme. If you do not have a child theme, create one.
- Step 2: Add the following code to the file and save.
[php]
// Disable XMLRPC
add_filter( ‘xmlrpc_enabled’, ‘__return_false’ );
// Remove Link From Head
remove_action( ‘wp_head’, ‘rsd_link’ );
[/php]
XML-RPC DDoS Attack
Hackers can create a botnet of WordPress exploiting the XML-RPC vulnerability. Then they perform an XML-RPC DDoS attack on a specific website to take down the site. This type of attack sends massive amounts of fake traffic to a website to intentionally use up all the hosting resources and cause the website to crash. This type of attack blocks anyone else from accessing or using the site as a result.
XML-RPC Attack: Brute Force
Under normal circumstances, server firewalls detect and block brute-force attacks after a large number of unsuccessful login attempts. Unfortunately, this WordPress XML-RPC feature performs thousands of login attempts with a fraction of the requests to the server making it very difficult for the firewall to detect the attack.